Book traversal links for 2.2. Identity Proofing and Enrollment
2.2. Identity Proofing and Enrollment
Effective from 31/10/2022Identity proofing and enrollment (with initial binding/credentialing) constitute the first stage of a digital ID system. This component is directly and most immediately relevant to LFIs’ customer identification and verification obligations under Article 8 of the AML-CFT Decision. For illustrative purposes only, Figure 1 below presents a sample process flow for identity proofing and enrollment; the discussion that follows explains each step in greater detail.
Figure 1. Identity Proofing and Enrollment
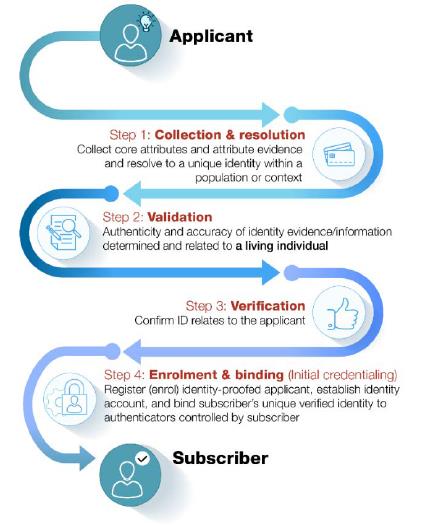 Source: The Financial Action Task Force5
Source: The Financial Action Task Force5Identity proofing comprises three actions: (1) collection and resolution, (2) validation, and (3) verification. Examples of each of these actions are included in the discussion below for illustrative purposes only; there is no expectation that LFIs employing a digital ID system for CDD use any particular method of identity proofing unless otherwise required.
| 1. | Collection and resolution involves obtaining attributes, collecting attribute evidence, and resolving identity evidence and attributes to a single unique identity within a given population or context (a process known as “de-duplication”).6 | |||||||
| ○ | Attribute evidence may be either physical (documentary) or purely digital, or a digital representation of physical attribute evidence (such as a digital representation of a paper or plastic driver’s license). Identity evidence has traditionally taken a physical form and been physically presented by the person seeking to prove his or her identity (known as a “claimant”) to an identity service provider (“IDSP”). However, with the development of digital technology, identity evidence may now be generated digitally (or converted from physical to digital form) and stored in electronic databases, allowing the identity evidence to be obtained remotely and/or identity evidence to be remotely verified and validated against a digital database. | |||||||
| ○ | Attributes may also be inherent, that is, based on an individual’s personal biometric characteristics, including: | |||||||
| • | Biophysical biometrics, such as fingerprints, iris patterns, voiceprints, and facial recognition—all of which are static; | |||||||
| • | Biomechanical biometrics, such as keystroke mechanics, which are the product of unique interactions of an individual’s muscles, skeletal system, and nervous system—all of which are dynamic; and | |||||||
| • | Behavioral biometrics, such as email or text message patterns, mobile phone usage, geolocation patterns, and file access log, which are based on an individual’s patterns of movement and usage in what are known as “geospatial temporal data streams.” | |||||||
| ○ | Under Article 8.1 of the AML-CFT Decision and section 6.3.1 of the AML/CFT Guidelines for Financial Institutions, required identity attributes for CDD under UAE regulations and guidance include, for a natural person, the name (as in the passport or identity card, number, country of issuance, date of issuance and expiration date of the identity card or passport), the nationality, the address (i.e., the permanent residential address), the date and place of birth, and the name and address of employer (if applicable). | |||||||
| When verifying the Emirates ID card, either physically or by way of digital or electronic Know Your Customer (“e-KYC”) solutions, LFIs should use the online validation gateway of the Federal Authority for Identity, Citizenship, Customs & Port Security, the UAE Pass Application, or other UAE Government-supported solutions, and keep a copy of the Emirates ID and its digital verification record. Where passports, other than Emirates IDs, are used in the KYC process, a copy should be physically obtained from the original passport, which should be certified as “Original Sighted and Verified” under the signature of the employee who carries out the CDD process and retained. | ||||||||
| 2. | Validation involves determining that the evidence is genuine (i.e., not counterfeit, forged, or misappropriated) and that the information the evidence contains is accurate. Validation is performed by checking the identity information and evidence against an authoritative and reliable source to establish that the information matched reliable, independent source data or records. | |||||||
| ○ | For instance, in order to assess whether an individual’s physical identity evidence (such as a driver’s license or passport), or the digital images thereof, is genuine, an IDSP may review the evidence to determine that there have been no alterations, that the identification numbers follow standard formats, and that the physical and digital security features are valid and intact. | |||||||
| • | When utilizing a physical or digital copy of identity evidence such as an Emirates ID card for purposes of validation, LFIs are expected to review the evidence for physical or digital abnormalities or possible alterations and to make a determination as to whether the evidence has been altered or forged. | |||||||
| ○ | In order to assess whether such evidence is accurate, the IDSP may query the government issuing sources for the license or passport and confirm that the information matches. | |||||||
| • | As noted above, LFIs should use the online validation gateway of the Federal Authority for Identity, Citizenship, Customs & Port Security, the UAE Pass Application, or other UAE Government-supported solutions, to ensure that the information presented for validation purposes matches the information included in reliable databases or other sources. | |||||||
| 3. | Verification involves confirming that the validated identity relates to the specific individual being identity-proofed, including (but not limited to) through the use of biometric solutions like facial recognition or liveliness detection. | |||||||
| ○ | For example, if performing verification remotely, an LFI or other IDSP could ask the applicant to take and send a mobile phone video or photo with other liveliness checks, compare the submitted photos to the photos on the applicant’s Emirates ID, passport, or other valid documents, and determine that they match to a given level of certainty. | |||||||
| ○ | To tie this identity evidence to the actual (real-person) applicant, the IDSP could then send an enrollment code to the applicant’s validated phone number, email address, or another address that is tied to the identity, require the applicant to provide the enrollment code to the IDSP, and confirm that the submitted code matches the code sent. Such measures would verify that the applicant is a real person, in possession and control of the validated phone number. At this point, the applicant will have been identity proofed. | |||||||
The fourth and final action in the first stage of a digital ID system is enrollment and binding.
| 4. | Enrollment is the process by which an IDSP registers (or “enrolls”) an identity-proofed applicant as a “subscriber” and establishes their identity account. This process authoritatively binds the subscriber’s unique verified identity (i.e., the subscriber’s attributes/identifiers) to one or more authenticators possessed and controlled by the subscriber, using an appropriate binding protocol. The process of binding the subscriber’s identity to authenticator(s) is also referred to as “credentialing.” | |||||||
| ○ | An authenticator is something the claimant possesses and controls—typically, a cryptographic module, one-time code generator, or password—that is used to confirm or “authenticate” that the claimant is the individual to whom a credential was issued and therefore is (to a given degree of likelihood) the actual subscriber and accountholder. The likelihood that the claimant to whom a credential was issued is in fact the actual subscriber is a function, in part, of the strength of the authentication component; stronger authenticators, such as longer and more complex passwords, can increase an IDSP’s confidence that the claimant is in fact the actual subscriber. | |||||||
| ○ | A credential is a physical object or digital structure, such as a physical or electronic ID card, that authoritatively binds a subscriber’s proofed identity (via one or more identifiers) to at least one authenticator possessed and controlled by the subscriber. When a digital IDSP issues an authenticator (such as a password or PIN) and authoritatively binds the authenticator to the subscriber’s identity, the physical object or digital structure that results (such as an ID card) is a credential. | |||||||
| Typically, an IDSP issues one or more authenticators (such as a password or auto-generated code) to the subscriber and registers the authenticators in a way that ties them to the subscriber’s proofed identity at enrollment. However, the IDSP can also bind the subscriber’s account to authenticators provided by the subscriber that are acceptable to the IDSP. For example, users of the UAE Pass app are prompted to create a signing password while completing the verification step at a UAE Pass kiosk or through the mobile app. The IDSP can also bind a subscriber’s credentials to additional or alternative authenticators at a later point in time, as part of identity lifecycle management (discussed immediately below). | ||||||||
5 Available at: fatf-gafi.org/media/fatf/documents/recommendations/Guidance-on-Digital-Identity.pdf.
6 Some government-provided ID solutions include a de-duplication process as part of identity proofing, which may involve checking the applicant’s specific biographical attributes (such as name, age, or gender), biometrics (such as fingerprints, iris scans, or facial recognition images), and/or government-assigned attributes (such as driver’s license, passport, or taxpayer identification numbers) against the identity system’s database of enrolled individuals and their associated attributes and identity evidence to prevent duplicate enrollment.